By Bradley Elston
By Bradley Elston
September 20, 2022
BURLINGTON, ON
Learn the main idea and concept of a Virtual data room. What is it and what purposes such software is used for?
Virtual Data Room: A Comprehensive Guide for Beginners
All sorts of file storage facilities are commonly used to store documents: a personal computer or various systems like Google Drive. As long as files are locked away from prying eyes, they are quite secure. But how to protect them if you need to give access to a limited number of people you don’t know well? For example, confidential documents in various transactions, some financial reports, or documents related to tax or audit audits.
There are many similar examples when it is important to provide access to the documents, on the one hand, and to make sure they are not leaked or the person who leaked them will be found, on the other hand.
VDRs (virtual data rooms) are used for secure data exchange. They allow delimiting rights and access to the documents inside the system, creating a clear structure and organizing easy exchange and work with files both inside the organization (synchronization with AD/LDAP) and during interaction with contractors.
The data room offers a standard set of tools, such as viewing documents, downloading, sending for printing, sharing, etc. Protection of files inside VDRs is provided by differentiation of user rights, control of document lifetime, and logging of events. But the question is how to be sure that the information will not leak into the public domain, and how to identify the culprit in case of leakage.
Check the virtual data room review to get more information about this software.

The existence of clouds has made it possible for data to be accessed by almost anyone anywhere. With a Virtual Data Room that data is secure – rock solid secure.
What is VDR?
A virtual data room is a tool, usually set up for a specific time and purpose, that gives authorized users access to a secure database of documents, according to their permit rights.
Why is It Important to Use?
Initially, virtual data rooms were created as an alternative to physical data rooms in due diligence procedures during mergers and acquisitions. Before the era of broadband Internet access, the familiarization of possible parties to a transaction with documents was as follows:
● The seller would allocate or lease one or more rooms into which folders of paper documents would be taken down, and write down the rent or lost profits from the misuse of the rooms as an expense item.
● A schedule of room visits and paperwork for potential buyers (beaders) was drawn up, which, if their number was substantial, greatly increased the transaction time.
● If the beaders were from another city or country, their representatives went on business trips to world cultural centers and to industrial regions, wasting time on the road and money on higher travel expenses.
But the virtual data room solves the problem of time, cost, and convenience of accessing documents.
Currently, virtual data room services accompany the activities of companies in other areas, from providing information to partners of investment funds to obtaining certificates for medicines, that is, everywhere where it is necessary to provide convenient access to confidential information for a certain circle of people who may be thousands of kilometers away from each other.
How Can a Virtual Data Room Protect the Data?
A virtual dataroom can be used in almost any situation where a company needs to provide simultaneous access to confidential information to several people:
● Analyzing corporate records;
● Creation of document archive;
● Audit;
● Preparation of an initial public offering (IPO);
● Help with mergers and acquisitions;
● Searching and providing information for investors.
The technology works in the following way: any interaction with a document (opening, downloading, sending for printing, sending by mail attachment, etc.) provides the user with a personal labelled copy. The copy is visually indistinguishable from the original, the markings are not visible to the naked eye, and can only be recognized using a forensic tool. In addition to the invisible marking the document is assigned the following attributes: employee ID, time, date, IP, location, etc.
If there is a leakage, the compromised document is loaded into the system and its labelling is compared with the original document available in the system for analysis. As a result, the system identifies the most similar copy and its owner. Thus, allowing you to find the potential culprit of the leak.
Such a solution can be used for critical business events: mergers and acquisitions, audits, and IPO preparation handling the personal information of public persons, as well as for intellectual property protection.

The name “the cloud” actually describes a room full of servers that hold data and make it available via the internet.
While a person is working in the VDR, a system is recording every copy of the document. In case even a small fragment of text of any document stored in such an electronic data room is compromised, the owner can conduct an examination and unambiguously discover the name of the person who published it without consent. Such marking is absolutely invisible to users and nothing changes in their usual processes.
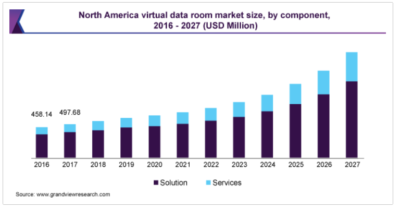
Market projections for VDR services is very positive.
Whether or not to tell employees or counterparties working in such a VDR about the presence of invisible marking is the right of the owner of the virtual room. On the one hand, this can immediately become a preventive psychological measure to protect documents. On the other hand, if the task is to identify an already existing insider, it is possible not to report about the technology.
Conclusion
A virtual room is a space where documents are sorted into folders, and all participants have a certain level of access rights. They can download files, and upload and share them only with permission. This format of use allows organizing convenient collaboration within different business processes.
VDR can save your company time and effort. When it comes to business effectiveness, every feature helps. The use of the dataroom software allows convenient managing of important corporate information and team collaboration. Also, it is more secure than usual file-sharing systems. So VDR is a smart solution for your business.